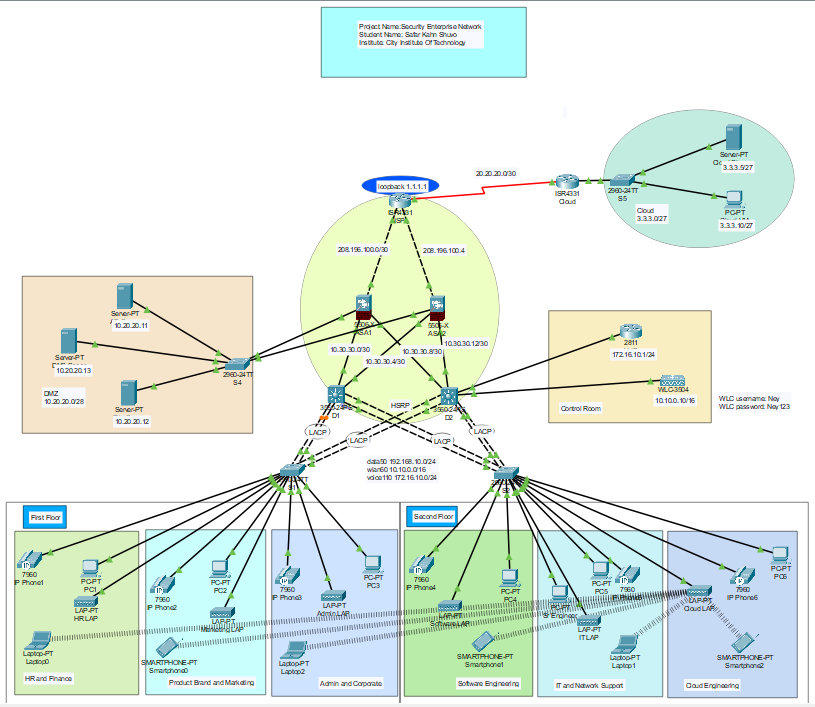
The primary objective of this project is to:
- Design a secure enterprise network architecture.
- Demonstrate communication between systems using routing and switching protocols.
- Implement and test security measures, including firewalls, VLANs, ACLs, and VPNs.
- Provide a scalable and redundant network for enterprise applications.
- Routers: Cisco ISR Series (e.g., ISR 2911) for routing and inter-network communication.
- Switches: Cisco Catalyst Series (e.g., Catalyst 2960) for VLAN and inter-VLAN routing.
- Firewalls: Simulated firewall devices for network perimeter security.
- Servers:
- Authentication Server (e.g., AAA Server).
- DNS Server.
- Application Servers (Web and Database).
- End Devices: PCs, laptops, and wireless devices connected through VLANs.
- Routing Protocols: OSPF/EIGRP for efficient network routing.
- Switching: VLANs (802.1Q) for logical traffic segmentation.
- Security Measures:
- ACLs for traffic filtering.
- Firewalls for access control.
- VPNs for secure remote communication.
- Routers:
- OSPF/EIGRP configuration for dynamic routing.
- NAT for external access.
- VPN tunnels for secure remote access.
- Switches:
- VLAN configurations for segmentation.
- Trunking for inter-VLAN communication.
- Firewalls:
- Rule-based access control for inbound/outbound traffic.
- Stateful packet inspection.
- Servers:
- DNS configuration for name resolution.
- Authentication services (e.g., RADIUS).
- Install Cisco Packet Tracer:
- Download from Cisco NetAcad.
- Open Project File:
- Clone this repository and load the
.pktfile in Cisco Packet Tracer.
- Clone this repository and load the
- Inspect and Configure:
- Open the devices in Packet Tracer to review the topology.
- Apply any necessary configurations (VLANs, routing, firewalls, etc.).
- Simulate:
- Use simulation mode to test connectivity and verify security policies.
- Document Results:
- Record test results and analyze the network's performance.
- Planning:
- Define the network's objectives, such as scalability, redundancy, and security.
- Design the topology and device roles.
- Implementation:
- Configure VLANs, routing, firewalls, and servers.
- Set up remote access through VPNs.
- Testing:
- Simulate traffic and validate network configurations.
- Verify ACLs, routing protocols, and connectivity.
- Optimization:
- Troubleshoot any issues and fine-tune configurations.
- Documentation:
- Maintain detailed records of configurations, addressing schemes, and test results.
Feel free to contribute or provide feedback! Open an issue or submit a pull request to improve this project.